Firewall rules
The global logical architecture of ShareAspace is the following:
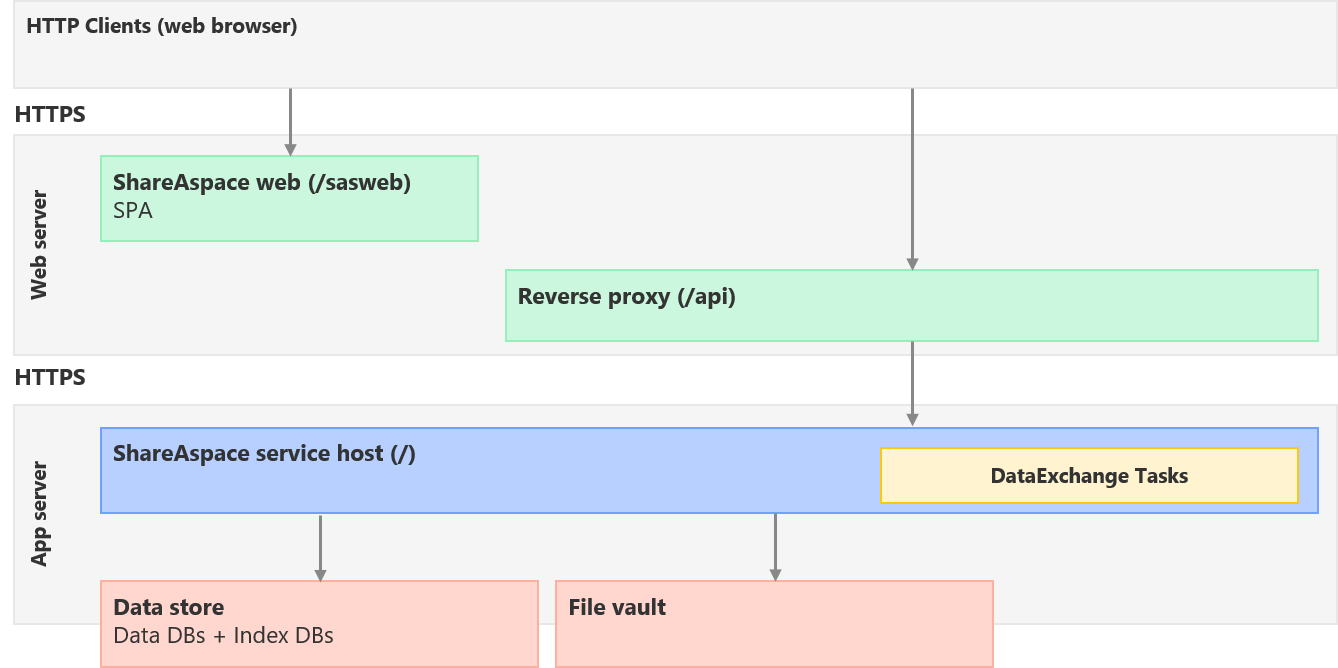
Note
All ports are configurable and can be changed.
Ports to open on firewalls
| Destination | Source | Port | Protocol |
|---|---|---|---|
| Web Server (IIS) / ShareAspace Web | Web Browsers | 443 | HTTPS |
| Web Server (IIS) / Documentation | Web Browsers | 443 | HTTPS |
| Application Server / ShareAspace Host Node | Web Server (IIS) / ReverseProxy(Gateway) | 5001 | HTTPS |
| Application Server / ShareAspace Host Node | Application Server / DataBackup Tool | 5001 | HTTPS |
| Application Server / ShareAspace Host Node Follower | Application Server / ShareAspace Host Node | 5001 | HTTPS |
| File vault Server | Application Server / ShareAspace Host Node | 445 | TCP/NETBIOS |
| Web Server (IIS) / External Extensions | Web Browsers | 443 | HTTPS |
| Web Server (IIS) / ReverseProxy(Gateway) | Web Server (IIS) / ShareAspace Extensions | 443 | HTTPS |
| Web Server (IIS) / ReverseProxy(Gateway) | Web Server (IIS) / Trusted External Extensions | 443 | HTTPS |
| Web Server (IIS) / Trusted External Extensions | Application Server / ShareAspace Host Node | 443 | HTTPS |
| SMTP Server | Web Server (IIS) / ShareAspace SMTP Mail Extension | 25 | SMTP |
Special case: failover setup
In the case where ShareAspace is setup with a cluster of Host nodes (see Failover principle), the following additional firewall rules need to be taken into account:
| Destination | Source | Port | Protocol |
|---|---|---|---|
| Leader Host Node | Follower Host Node | 5042 | TCP |
| Follower Host Node | Leader Host Node | 5042 | TCP |
Windows firewall setup
Beside environmental firewall settings, on Microsoft Windows Server 2019 (Application Server and Web Server) you will need to add Inbound Rules to the Windows Firewall.
- Port 5001 on the Application Servers.
- Port 80/443 on the Web Servers (those are usually set by default when installing the Web Server (IIS) Role).
- Port 445 on the FileVault (this port is usually automatically opened when setting file sharing on a Windows Server)
Caution
On the Application Server the following procedure will open up port 5001 completely.
This will allow you to access the Application Server from any client application. If
you are running the all the ShareAspace components (including the Gateway) on the
same machine as the Application Server, you do not have to open this port as HTTP clients
will contact ShareAspace via the Gateway.
To setup an Inbound Rule on Windows Servers:
- Open Windows Firewall with Advanced Security.
- On the menu on the left, Click Inbound Rules.
- On the Actions menu on the right, Click New Rule....
- Select
Port
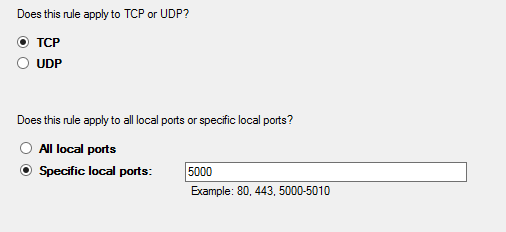
- Select
TCP - Set the specific local ports to open, for instance
5000
- Select
Allow the connection
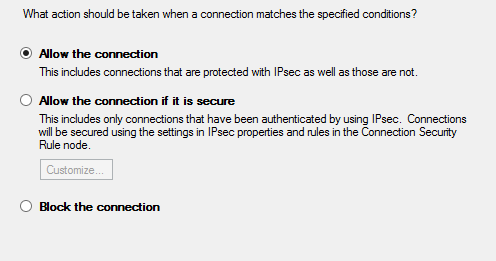
- Select,
Domain,Private,Public
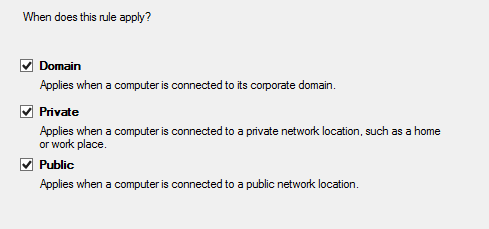
The Windows Firewall Inbound Rules can also be set using a Windows PowerShell script as follow:
Download set-firewall-rules.ps1
$NET_FW_PROFILE2_DOMAIN = 1
$NET_FW_PROFILE2_PRIVATE = 2
$NET_FW_PROFILE2_PUBLIC = 4
$NET_FW_PROFILE2_ALL = 2147483647
$NET_FW_IP_PROTOCOL_TCP = 6
$NET_FW_IP_PROTOCOL_UDP = 17
$NET_FW_IP_PROTOCOL_ICMPv4 = 1
$NET_FW_IP_PROTOCOL_ICMPv6 = 58
$NET_FW_RULE_DIR_IN = 1
$NET_FW_RULE_DIR_OUT = 2
$NET_FW_ACTION_BLOCK = 0
$NET_FW_ACTION_ALLOW = 1
$fwPolicy = New-Object -ComObject HNetCfg.FwPolicy2
$rule = New-Object -ComObject HNetCfg.FWRule
$rule.Name = 'NovaCluster'
$rule.Profiles = $NET_FW_PROFILE2_ALL
$rule.Enabled = $true
$rule.Action = $NET_FW_ACTION_ALLOW
$rule.Direction = $NET_FW_RULE_DIR_IN
$rule.Protocol = $NET_FW_IP_PROTOCOL_TCP
$rule.LocalPorts = 5001
$fwPolicy.Rules.Add($rule)